Attacking Wifi with Wireshark
For a
thing
, I want to dump the wlan traffic between an Android app and a
wifi camera. It isn't hard to grab network traffic from Android, if you have a
rooted device you can just run
tcpdump
.
tcpdump
on Android is annoying, you
have to manage the pcap files and it isn't clear what you are capturing.
Thankfully,
wireshark
can be fed
WPA and WEP keys
, making snooping as a
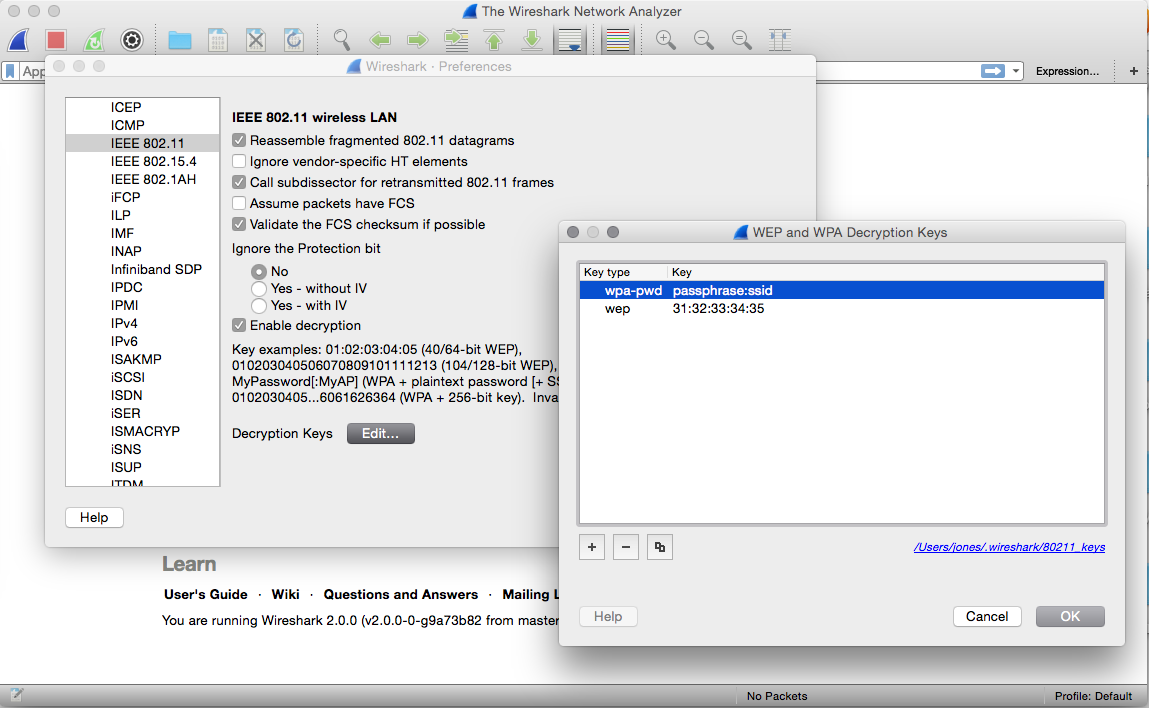
third party an absolute breeze. The key options are in the protocol preferences
for
IEEE 802.11
, they look something like this:
wep:a1:b2:c3:d4:e5
wpa-pwd:MyPassword:MySSID
wpa-psk:0102030405060708091011...6061626364
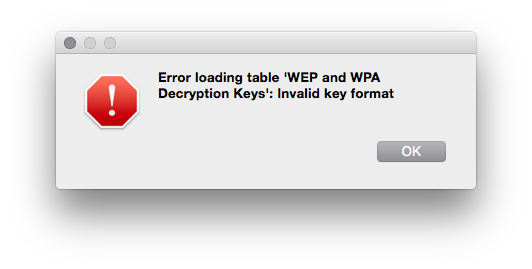
The protocol preferences dialog doesn't seem to do any validation of the keys,
instead I had to restart
wireshark
to get the super unhelpful error message.
The
wireshark
guide mentions the wireless toolbar, but this wasn't available
on my platform and I didn't need it. With just the key, WEP traffic can be
decrypted. WPA traffic requires that you capture an EAPOL handshake first. The
easiest way to do that is observe the device keying, for testing I just had my
phone join the network.
Reading: Nemesis Games, All Tomorrows Parties